
WEIGHT: 53 kg
Bust: 2
1 HOUR:70$
NIGHT: +30$
Services: Female Ejaculation, Mistress, Swinging, Massage prostate, Bondage
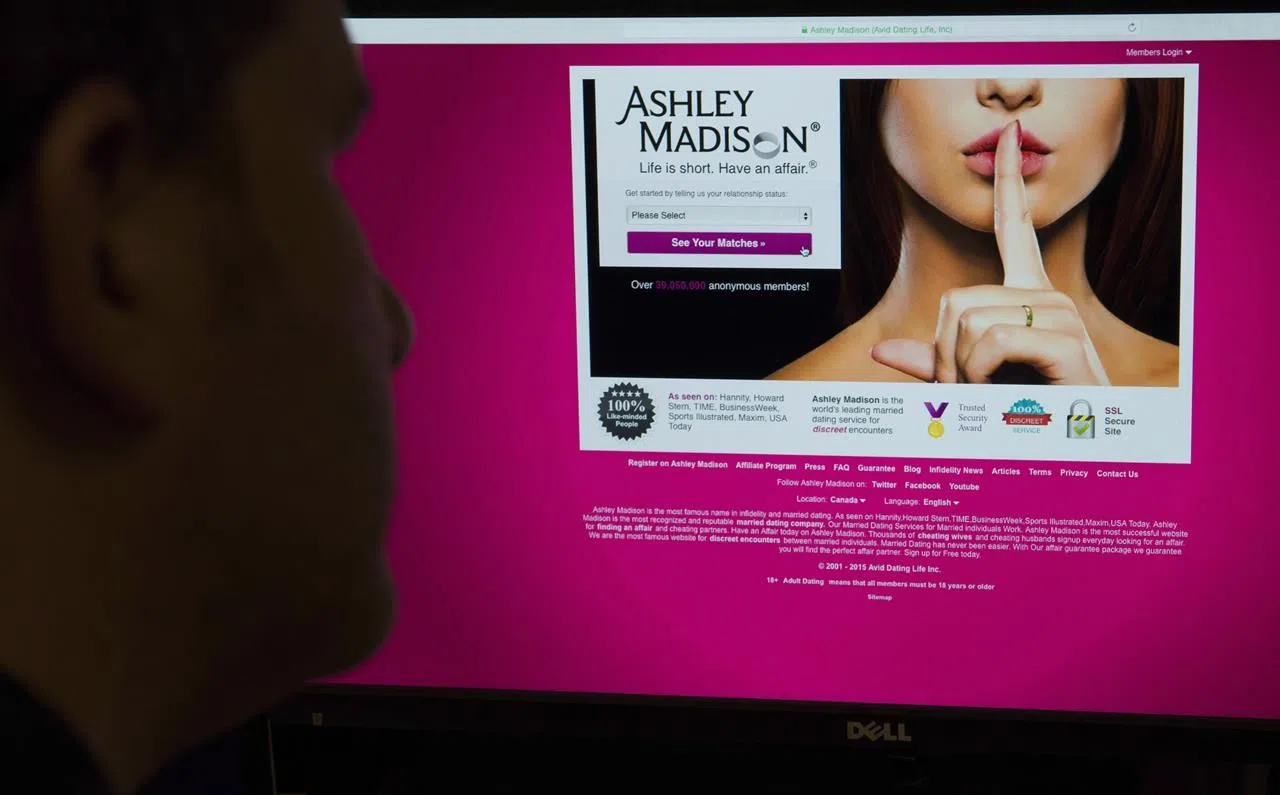
Today it has been confirmed that AshleyMadison. The Impact Team are demanding that Ashley Madison and its partner site Established Men be shut down, having already posted some of the stolen data online.
We've asked our Forensic Manager, James Allman-Talbot, about what happened, what this means for Ashley Madison's future, and how it could have been prevented. The Ashley Madison case has hit the media today. This was clearly a very targeted attack — how often are attacks like this seen against individual companies? When it comes to payment card data breaches, hackers are somewhat unlikely to target a specific company and will instead pick their targets at random, usually using a piece of software that will scan all web servers on the internet for known vulnerabilities that they can subsequently exploit.

Now that the data is in the hands of the attackers, how would Ashley Madison be able to firefight against the data leaking online? Once the data is outside of their area of control, it is impossible to determine where it may end up or what may happen with it. Ashley Madison have stated that they are using the Digital Millennium Copyright Act DMCA in order to serve takedown notices to anyone found to be hosting the leaked data online, although this will only be effective with law-abiding websites that will act on the notice.
It also relies on Ashley Madison being able to identify every single copy of the data hosted online, which is an unlikely scenario. Although they may be able to limit the exposure, it is certainly impossible to guarantee that the data will never be leaked online - only the attackers that obtained the data will be able to do that.
Could this attack have been prevented? If so, what were Ashley Madison doing wrong? Things like file integrity monitoring, malware scanning and a web application firewall can give websites the controls they need to either prevent a breach, or detect a potential breach as soon as it occurs.



































